ARCHITECTURE FOR COMPUTING INFRASTRUCTURE
This is the third part of writings in introduction to FINDEF ICT rationalization that took place between 2004 - 2008 from Enterprise Architecture viewpoint.Evolutionary outcome of few decades of military computing
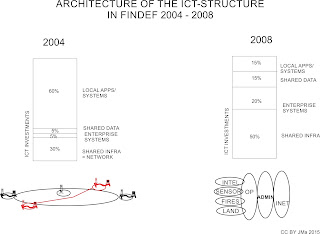
The structure of computing in FINDEF by 2004 was a result of decades of evolutionary sediments. There was Mainframe (MF) computing providing terminal sessions over remote connections. There were number of stand-alone PC’s providing platform for many special applications for individual needs. There were VAX/VMS, SUN UNIX, Windows Server, IBM OS2 and Novel Netware client-server systems build for specific information system. Since 1995 there had been efforts to standardize this infrastructure but since computing was mainly owned by military branches and Services, there was no will or resources enough behind the rationalization. Most of the computing happened in each garrison within the reach of Local Area Network (LAN). Only Mainframe and some Human Resources related information systems were centralized as depicted in Figure 16.
Figure 16: The AS-IS situation of FINDEF computing in 2004
This structure hyped with over 130 medium or bigger computing sites (over 50 users each), each hosting over 20 bigger information systems, average number for administration tasks was 3000 per site. There were over 300 different information systems, 5500 different applications, over 600 vendors, about 10% of total personnel and about 10% of annual budget in providing information related services in FINDEF. These services were supporting mainly (75%) administrative functions and not core functions.
The analysis of linear continuum of this evolution forecasted unpleasant future for computing of FINDEF :
- There are no more resources to support maintaining this heterogeneous infrastructure in FINDEF
- The lack of resources and competent personnel is hindering the improvement of network enabled defence capabilities for FINDEF
- As the complexity of Information technology increased it might become cost-effective to out-source IT support to partners
- The competence of personnel in FINDEF is not sufficient to maintain heterogeneous IT infrastructure as complexity is distributed in all garrisons.
- There is no base to build interoperability between Services, with other governmental agencies, with partners or with international allies since data is scattered in hundreds of dedicated information systems
- The FINDEF is not able to comply with requirements of Information society program by the Government of Finland.
This analysis provided enough evidence to commence the transformation and create the sense of urgency called after in Kotter’s (1996) Leading change.
New computing architecture for FINDEF
The idea for future computing concept was to gather most of the computing inside the core network and simplify the client in terminal device to degree that it is maintainable by end user. This required continuous connectivity to core computing services. The change in information management was actually requiring different connectivity also since data was born mostly in numerous systems and collected data warehouses. This ended up that no one man was able to make sense nor make decisions disconnected.Core computing was done in metro information powerhouses, where presentation logic, applications and databases resided. Only thin client remained in end user terminals. Information powerhouses were categorised to centralized datacenters and regional datacenters according to survivability and scalability requirements. All three core computing layers created each a network in which both availability and performance was more scalable. Just by adding storage or processing units to already distributed structure, one was able to adjust the survivability as crises evolves or performance as need for storage or processing power appears. The information powerhouses provided a common session support and standard client platform to all applications. All sessions were protected with virtual private network connection. All clients were maintained with MS system management solutions. All sessions were identified and access granted based on strong identification via smart card. All application had same presentation layer provided by portal where role based access was categorising users first time. Then the actual servers and business applications were consolidated with three different solutions within information powerhouses:
- Data center cabinet as a service was lowest level arrangement where the server was consolidated as-is from its remote location. Only power, cooling and infrastructure management was provided by information powerhouse and its personnel. Otherwise it remained under the responsibility of original owner. This status was given to servers that had more than 3 years but less than 5 years hardware life cycle left. Presentation layer was normally terminated at second layer with Citric Metaframe so client was changed to browser based.
- Platform as a service, where existing applications were substituted with ones that were running over provided standard platforms. Those platforms were enterprise solutions as Lotus Domino, MySAP, CISCO computer telephony integration or IBM WebSphere. The standard terminal configuration included client software for these platforms. This was provided to those systems with less than 3 years of life cycle remaining.
- Software as a service was provided from information powerhouse to replace a number of different applications. Process owner had to choose from provided list what application she preferred and then information powerhouse provided these applications as on-demand service. Process owner was released from other responsibilities and rights concerning applications, infrastructure and their maintenance.
The TO-BE architecture for FINDEF computing infrastructure is illustrated in Figure 17.
Figure 17: The planned computing architecture for 2007 onwards in FINDEF
The migration from distributed and stove piped structure towards more centralized and flexible structure took four years and several steps in improving the competence of personnel.
Consolidation of military computing in creating flexible infrastructure for network enabled defence
Consolidation of the FINDEF computing was divided into two main courses of action depicted in Figure 18. Enterprise resource management area of military affairs was consolidated from all those information systems and networks that were categorised as administrative or supportive computing. This environment was optimized to support client-provider value chain that extended beyond the borders of FINDEF. It was also optimized for effective force production and force support. The consolidation was a migration from over 100 garrison based computing sites either to less than 10 regional sites or directly to three main data centres. Where the Application Service Provider (ASP) maturity of technology and processes were achieved, there outsourcing to Provider Partner was considered. The leading idea was that outsourcing problems before solving them at least at process level is not a long-term solution.Figure 18: Consolidation of the computing of FINDEF
As the consolidation of administrative information technology was phased first, there was also requirement for this program to release human resources to execute the second course of action in operational computing. This environment was heading towards integrated command and control structure where main process relationship would be supporter – supportee. It was also to enable do more with less resources as combined arms fires, joint logistics and flexible decision making.
The migration was from unit and arms specific systems towards “cloud computing” structure of about ten data centres that would provide both operational and tactical applications as service besides the organic applications hosted in each unit. This was to enable more flexible use of information in each phase of operation and readiness of defence. Thus Air, Navy and Land command and control systems were hosted AS-IS in operational data centres being forced to exchange data via joint level command and control system. Surveillance and Reconnaissance systems were connected to operational cloud besides their parent units thus enabling the collection and fusing of multisensory picture for enemy tracks. The consolidation in operational environment was to end with separate domains for fires, command and control and sensing.
Together the two main environments for operations and support created the foundation for networked enabled defence: Value chain for both Teeth and Tail enabled with information. This end was to provide ability to use different specialized units together in mission; enable flexible cooperation with different governmental and non-governmental agencies within international context and finally achieve the strategic goal of flexibility in facing whatever surprise adversary and situation might produce.
The consolidation of computing was visible also to end user when the devices of their everyday workplaces changed. This proved right the clause of “Everybody is ready for changes, but nobody wants to change” or as Aristotle says “We are what we repeatedly do”.
Tangible results visible to all end users
The personal and branch driven evolution of electronics was visible on the table of administrative end user. The sedimentation over 10 years of personal computing was evident as each user had in average three personal computers with printers and other peripherals. He was also provided with 2-3 different telephones. He had a number of copiers, scanners and facsimiles available in his office. The maintenance and sustenance of all this electronics was overstretching both available personnel and budget. The change faced by average end user in FINDEF through 2004 – 2008 is illustrated in Figure 19.Figure 19: Rationalization of administrative ICT devices provided to end user through 2004 – 2008
The biggest change was provided when Internet workstation was replaced by Internet as a service within administrative workstation. This was done in information powerhouses where 30 000 Internet users were terminated with Citrix metaframe and the connection was provided as a service to all administrative users. Since operational environment was providing a special laptop computer for mobility, all administrative PC’s were consolidated into one machine with either 5 years lifecycle provided by C4I Agency or 3 year lifecycle provided by a leasing company. As computers were replaced either within 3 or 5 years FINDEF also got rid of unnecessary busy work during updates of major operating system and excess on-site support.
The other bigger change was the centralization of printing, scanning, copying and faxing. This was again provided as a service by C4I Centre with good support of partner. All peripheral devices were consolidated into department or unit centred multifunctional machines. Costs was transformed from fixed to flexible so expense was only from usage rather than investment. Service was provided as turn-key solution including papers, ink, cartridges and maintenance. It affected about 14 000 users and replaced about 9 000 different peripherals with 2 000 multipurpose machines.
Telephony service was also rationalized since average user was not utilizing the added services provided by fixed digital ISDN phone. Together with ISDN-phone the large network of ISDN branch exchanges was also dismantled. More modern mobile telephony service provided by a partner was decided to use for military administrative purposes. Only a small number of analogue telephones was to remain for providing special needs. Operational telephony users were provided with TETRA services and computer integrated collaboration applications in their laptops.
Since end user changes do create the biggest opposition there was important to get the highest level sponsorship behind these transformations. The commander of FINDEF together with all Generals were the first to use new services thus showing example to all personnel. Chief Information Officers in each Service were leading training and awareness sessions and made themselves the “super users” of new devices and IT services showing hands-on to the personnel the example in improving every day knowledge work.
This ends the third part focusing on transformations in computing architecture. The next part is describing the changes in command post architecture of FINDEF.