Utilization of Enterprise Architecture approach in major transformation of Military Affairs and ICT services in Finland 2004 - 2008.
This is the first part of series of writings under this title!
This is the first part of series of writings under this title!
SUMMARY OF THE TRANSFORMATION IN FINNISH DEFENCE FORCES (FINDEF)
In preparation for the improvement of the Military Affairs
by 2008, there was initiative for preparing the branch of 6 (Communications and
Information Systems) to better enable joint and interagency operations within
Finland. This program was named The Rationalization of Information Management
in Defence Forces (TIERA[1]
in Finnish). Program was executed in three phases: I initialization, II
preparation and III implementation. This paper is focusing on the phase III –
Implementation.
The foundation for transformation was laid in the Finnish
Security and Defence Policy 2004 white paper stating that:
- Organization and command structure of the FINDEF will be flattened;
- Command and Control of Defence will be renewed and integrated;
- Administrative information management of the FINDEF will be rationalized.
These strategic guidelines meant that diversification of Services, Commands and
Branches will end and Defence Forces shall start transformation towards more
flexible, joint and networked organization. New performance was to be found
from unification and coordination of military affairs strategy as depicted in
Figure 1.
Figure 1: Major transformation of organization and strategic
affairs in Finnish Defence Forces 2008
Coordination was needed with joint operations and over distributed
command of regional defence in all traditional operational dimensions.
Unification was requested in having more streamlined support and force
production functions. Transformation in military core affairs was calling after
restructuring the whole information management and command systems that were
mainly built to support separate functions per Service or Branch of Military. Rationalization
also meant that administrative information management was to be provided as
common service to all Services and Units within the FINDEF and its strategic
partners.
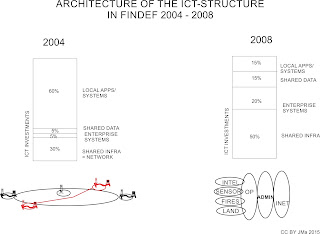
Transformation in Military Affairs was seeking after the redesign of the ICT-structure starting from network topology, providing shared information for “one truth within enterprise” and standardizing most of the business applications at enterprise level. Figure 2 is showing the change from 2004 garrison based “stove pipe” information systems to Enterprise wide platforms, where specialization of the Services were still followed at tactical level. Consolidation of information technology was achieved by concentrating first to administrative and internet domains. As they were releasing resources, focus was turned towards operation and tactical domains. This provided also strategic transformation of resources from support towards core affairs in defence.
Figure 2: The transformation of ICT Architecture in Finnish
Defence Forces
The 2008 ICT structure was providing more secure information
and processing services both to peace time force production, international
operations, interagency co-operation and war time intensive combat. Joint
ICT-service provider, C4I Agency of Defence Forces, was established to provide
services that enable flat command structure and joint and interagency
operations in robust and survivable manner. Local applications and systems were
consolidated and their ownership transferred to C4I Agency, which executed very
strict elimination/substitution process at technology level. The ICT-structure
of FINDEF was divided into seven remaining domains: 1.Internet,
2.Administration, 3.Operations, 4.Intelligence, 5.Sensors, 6.Fires and 7. Land
tactical.
In the end of transformation most of the infrastructure,
systems and data was operated by Joint ICT-service provider. The Services and
Branches remained in charge of processes, information and knowledge. The Services
also were to improve their tactical and battle technical capabilities. ICT
investments were managed at enterprise level with capability portfolios. All
joint and common ICT-systems were provided as a service (SaaS).
VISION FOR SMARTER DEFENCE FORCES
Stove piped approach did not produce major capabilities
The white paper for Finnish Security and Defence Policy 2001[1]
declared that:
"The first stage of the development programme will be the issuing of procurement authorizations for intelligence, surveillance and command and control systems in the period 2000-2005. The main procurement projects concern mobile electronic intelligence and surveillance units, combining the data transfer systems of each of the services, information system integration, and modernization of the Air Force surveillance and command and control system to bring it up to par with the performance of the interceptors."
By 2003 though there had not been any major advances in
combining data transfer systems or integrating information systems. Every
service and branch was improving their own structure and capabilities without
common strategy. It was evident that ruling culture of diversification needed
to be changed with more drastic means.
Clear vision in context of a bigger picture
The creation of vision started early 2001 when first workshops were launched in
drafting a business concept for networked military force modelled in Figure 3.
Vision for modern military affairs was based on eTOM[2]
business model since it captured all aspects of networked business and value
chain. Customer was replaced with
Adversary and value stated as “effect in adversary’s system”. Operations was
translated to force utilization and strategy to building readiness. Force
support was already in the model as it is formed from networked business model.
Management was changed to strategic planning covering the whole networked force
with all its stake holders. Relationship management layer was turned to effect
delivery. Services layer to teeth of combat i.e. combined arms capabilities.
Resources layer was called management of resources and tail indicating both
troops in operation and their supporting elements both in logistics and troop
production. Supply chain layer was called chain of value in total defence. This
indicated Defence Forces need to control the whole chain of value used to
enable and deliver military effect.
Figure 3: New concept for military affairs using eTOM
framework for digital enterprise
Shareholders were recognized as Government and Citizens closing
the sides of Clausewitz’an triangle[3]
and extended with personnel of Defence Forces. Strategic capabilities were reduced
from the model by running a number of war games against different adversaries
in various scenarios. Strategic capabilities of digitized Defence Forces were
defined as:
- Effect based: Contrary to plain attrition of adversary force, the effects are directed to essential nodes of adversary’s force system which causes adversary to lose its capabilities exponentially.
- Plug and shoot: networked arms and sensor platforms together with troops that can be manoeuvred around the area of operation to avoid being destroyed by counter fire. Still they are plugged promptly to sensor and fires networks and able to deliver their effect in time and place.
- Plug and manage: a continuous flow of Command, Control, Communication, Intelligence, Surveillance, Target Acquisition and Reconnaissance information flow and services that enable plug command posts into operational network and start conducting operations and tactical tasks.
- More together: a network of resources that can be tapped as needed and orchestrated with strategic and operational awareness to maximize the effect and support to forces.
This flexible model for military affairs was based on
strategic strengths of faster learning and higher level of soldiers together
with moral high ground of defending one’s own country.
Experimenting to gain assurance for some key components of new structure
This vision was tested in exercises and development projects[4]
in Northern Command during 2001 – 2004. The intermediate report from Northern
Command on 2002 was proposing a technical and process blueprints for future
Command, Control, Communications, Computers and Information structure. It also
provided a concept for distributed command post structure that provided
survivable and continuous management of Defence Forces. A transferable
Operation Centre (TOC) was one of the experimental projects launched.
The TOC project was funded in the traditional way. The
budget plan for years 2001 - 2005 was laid out in 1988. The project was given a
task to rethink the whole concept from beginning and not necessarily follow the
linear armament development approach. A spiral development method was chosen
since objectives were not clear and capability target was moving. The first
spiral was very careful minimizing all risks. It build a great confidence since
the second cycle aimed to serve a very important exercise. After success, all
levels of concept got speed into their development cycles and new innovation
was introduced specially at the process level.
Information technology parts provided the most opportunities
during the first two cycles, but afterwards the process level gained most
results and enhanced the command and control in very profound manner – changing
the method of staff work itself and not only the tools around Headquarters.
The TOC project provided an example of iterative development method where the objectives of each cycle were adjusted according feedback from Command post exercises. The project did achieve capabilities that were not imaginable in the year of founding (1998) but within the budget and timetable as anticipated. Figure 4 describes the cycles of spiral development in TOC project.
Figure 4: Development spirals of TOC development between
2001-2003
Experimenting provided needed assurance in:
- A Survivable Command Post concept
- Operation and execution processes that enabled distributed plug and manage concept
- A concept for “cloud computing” services and transferable provision of ICT services
- A spiral Development Method that provided controlled means to achieve goals that were not precisely defined.
Setting goals at highest level to gain authority for transformation
The transformation of Military Affairs in Finland was
defined in the white paper of Finnish Security and Defence Policy 2004[5].
It declared the following goals to guide the change:
“Command of the smaller, more mobile wartime forces in the 2010s requires a situation picture as real-time as possible. To ensure correctly timed command arrangements, an integrated intelligence, surveillance and command and control system will be developed for the Defence Forces. This will enable the common real-time situation picture to be communicated to every service and the creation of sufficient communication links. The command and control system will be internationally interoperable.”
“The Defence Forces’ information management system will be rationalized. The new information technology platform will be divided into operational and administrative environments by the end of 2009. The administrative environment will be highly centralized, allowing allocation of resources to meet the needs of the operational information technology environment and also to enable other security authorities (determined separately) to be linked as users into the system.“
These two statements provided the highest sponsorship to
start transformation of both Command and control (C2) structure and ICT
infrastructure of the Finnish Defence Forces.
Firstly it launched the analysis of the strategic attributes
for the transformation of command structure. Analyses was already started with
earlier pilot programme for transferable command post but now it was extended to
the Defence Command and its’ Research Centre. Focus was given to intelligence
and situational awareness; target acquisition and fires; command, control and
battle management; management of support and resources illustrated in Figure 5.
The core C4ISTAR processes were supported with enablers as:
- Virtual execution: No key C2 process function should be too dependent on any site, time, system or specific people as it might be a single point of failure. Virtuality of structure and functions should provide the resiliency required in special area of operations in Finland.
- Flexible change of execution: If any command post, any troop, any weapon platform in any situation gains advantage over adversary, there should be ability to support that entity with other force elements available. Any feasible improvised means of countering adversary should be exploitable through the force.
- Competence Acquisition: Ability to learn and adapt to evolving situations. Systematic learning needed to be supported. This meant enabling both individual, team and machine learning during operations.
- Knowledge Management in four different situations:
KNOWN – existing structured and unstructured
information is available to all
authorised users.
KNOWABLE – Reachable data is available for
experimenting, expert analyses,
fact-finding, and scenario planning.
Collaboration between decision makers and
subject matter experts is
accelerated.
COMPLEX – active and forceful reconnaissance is
connected with decision makers
and different experts to enable modelling –
probing – recognition – decision cycle to
be faster than adversaries.
CHAOTIC – decision makers are trained with a number of situations, decisions
and
analyses of outcome and made familiar with the features of area of
operations.
Figure 5: The approach for improvement of C4ISTAR in FINDEF
These enablers and attributes were supported by three
parallel structures of ICT services:
- Situation services focused to share information on current situation and managing structured transactions
- Voice services focused on enabling flexible collaboration with voice, video, chat and application sharing thus providing means for informal communication.
- Content management services providing support to formalised, unstructured information management.
The three structures were built strategically parallel and
to a degree independent thus providing reliability to digitalized C4ISTAR functions.
There were no analogue or manual substitutes available in fully digitalized
command structure unlike in previous generation command and control system of 1990’s.[6]
The white paper of 2004 was calling after “The new information technology platform will be divided into operational and administrative environments by the end of 2009.” This provided the strategic level views for information domains and policy in Enterprise Architecture: Tactical domains, Joint operational environment, Administrative environment and eFinland environment pictured in Figure 6.
Figure 6: Vision for strategic information environments and
their connections in FINDEF
These information domains were to be connected
with secure gateways (GW) to allow information flowing in supporting force
utilization and out to enable support and force production. Internet based
services were to be used from Administrative environment in secure way. Administrative
network based services were to be used from Joint operational environment. Services
in tactical networks should be hosted both on joint operational infrastructure
and on tactical platforms. The vision also predefined that outsourcing was to
be used in improving cost-efficiency of ICT service production and in releasing
in-house resources to be used more in joint operational environment.
STRATEGY FOR TRANSFORMATION
Major thresholds
The strategy for transformation of military affairs in Finland was divided into
three phases illustrated in Figure 7:
Figure 7: Strategic phasing of transformation of FINDEF
- ICT Rationalization (TIERA) 2004 – 2008 creating enabling infrastructure for other affairs to be changed. Focus was both on technical development but also improving the ICT service provider maturity. Subprojects included for example Rearranging the network infrastructure, Consolidation of common services in Administrative environment and establishing joint operational environment providing simple information services empowered with collaboration and content sharing.
- Development of both operational and support functions of FINDEF with two programs of:
Integrated Command, Control, Communications,
Computers, Information,
Surveillance, Target Acquisition and Reconnaissance (iC4ISTAR) 2004 – 2010
focusing on improving force utilization and
Enterprise Resource Management (ERM) 2005 – 2012 focusing on enabling
force production and support.
Network Enabled Defence 2006 – 2015 where joint and common enablers will support FINDEF to reach towards greater capabilities that provide strategic advantage. This phase was calling after new innovations and research to exploit new capabilities at military levels of tactics, operations and strategy in pursuing towards advantages over possible adversaries.
Surveillance, Target Acquisition and Reconnaissance (iC4ISTAR) 2004 – 2010
focusing on improving force utilization and
Enterprise Resource Management (ERM) 2005 – 2012 focusing on enabling
force production and support.
Network Enabled Defence 2006 – 2015 where joint and common enablers will support FINDEF to reach towards greater capabilities that provide strategic advantage. This phase was calling after new innovations and research to exploit new capabilities at military levels of tactics, operations and strategy in pursuing towards advantages over possible adversaries.
The challenge of these kind of transformation was captured
from Gartner Group saying that there are two major caps to overcome on the journey:
- First cap is preventing the development of joint functions. This is predominant in enterprises that are diversified with long cultural legacy. This call after the change of power structure within enterprise as “stovepipe” ownerships, investments and service production diversifies the whole of organization.
- Second cap is preventing the development of joint capabilities. This calls after new ways in approaching adversary, projecting force and effecting in adversary’s system and utilization of force. Militaries throughout the history have struggled with this doctrinal transformation[1].
Campaign plan
The strategy in overcoming these major thresholds included major organizational
changes on 2008 to close some strong organizations and create feeling of inevitable
change within FINDEF. Leverage for transformation was provided also from outside
of FINDEF with program for information society. Government was running this
program to change the governance towards enterprise approach, improve the
services towards citizens and enable transformation towards information
society. This provided necessary outsider to drive development, interagency
co-operation and integration with society. The campaign plan presented in Figure
8 was aiming a stage where information would be considered as an asset and also
as a weapon. Journey towards these goals should be taken with small development
steps. No revolutionary approach but merely accelerated evolution.
Figure 8: The campaign plan for transformation of FINDEF
The in-house transformation of FINDEF ICT structure included
parallel experimenting and testing for new possibilities in defence and
changing the existing ICT infrastructure. Plan called first the rationalization
of administrative information environment and streamlining the support
functions in military affairs. Experienced and more competent professionals
were then focused to develop joint operational environment and integrate
tactical domains with it. The new platform was planned to enable joint,
interagency and information operations. As 2004 white paper for security and
defence policy was providing the jump start declaration, there was 2009[2]
white paper providing acceleration to transformation proclaiming that:
"The Defence Forces command, control, communications, computers, intelligence, surveillance and reconnaissance (C4ISR) systems generate an integrated military situation picture (land, sea and air as well as information and the IT environment). The national system is utilised to expedite planning, command and control and execution. Defence capability against an adversary’s cyber attacks is maintained and improved. The nationwide logistic system taps into the resources of the entire society in supporting military defence."
White paper set goals to integrated situational picture
including the “cyber” dimension, protection against cyberattacks is improved
and logistics is extended to reach further to defence value chain.
Enterprise architecture
The campaign plan was supported with enterprise architecture planning. First
architecture project was established early on 2004 first to define existing
structure but quickly it become means to provide orientation in strategic
decisions during the journey. The enterprise architecture was divided into substructures
presented in Figure 9 and partner to create integrated project team was chosen
on late 2003.
Figure 9: Enterprise architecture subdivision in supporting
the ICT infrastructure transformation
The planning of architecture was managed from two parallel
dimensions: architecture team and business team. Architecture team was focusing
on information systems and services layers whereas business team was supporting
with business models and processes. Integration, platform and connectivity was
planned within each executing project (Networks, Hallnet and Opnet) and firmly
governed by J6 division (program office) in Defence Command.
Besides the main reference architectures for administration and joint operations there were also subsets for Internet based services, interagency enablers, strategic partners and international interoperability efforts. They did not have their own reference plans but were defined features in other references. Tactical information environments were managed in operational reference architecture domain as pictured in Figure 10.
Besides the main reference architectures for administration and joint operations there were also subsets for Internet based services, interagency enablers, strategic partners and international interoperability efforts. They did not have their own reference plans but were defined features in other references. Tactical information environments were managed in operational reference architecture domain as pictured in Figure 10.
Figure 10: A view to reference architectures of FINDEF
The following chapters will illuminate further the
substructures of enterprise architecture of FINDEF as the transformation was
planned and executed.
This ends the first part of the paper on ICT transformation in FINDEF during 2004 - 2008 from enterprise architecture viewpoint.










No comments:
Post a Comment