What combinations of men and machines may create a better effect in battle when artificial intelligence is introduced into 3rd generation military-industrial systems?
Introduction
Military organisations have an advantage over other organised violence in generating balanced socio-technical systems. They control the force generation life cycle from R&D to lessons learnt of troops (human-machine teams). They can acquire elements and abilities from their national sources. Specifically, the monopoly in organised violence advantage enables the development of culture, competency, process, data, and technology in coordinated steps, experimenting with different combinations and keeping up with a continuous but balanced improvement.
Armed Forces can generate competent socio-technical systems from specialised components. Through cooperation, they can project power over a broader spectrum of warfighting domains (multi-domain operations) , balancing one arm's weakness with the strengths of other arms and services. Naturally, these socio-technical (Trist, 1981) force structures need lots of training, trust building, and interoperability exercises before the system's effect appears on the battlefield. Still, human remains the hub of these industrial systems. The adversary tactics aim to disrupt the morale cohesion of opposing troops and operational art to outplay the opposing commander's options in her playbook.
What happens when a 4th generation industrial artificial intelligence is introduced into the above 3rd generation socio-technical force? Humans are emotion-driven, irrational decision-makers (Kolbert, 2008) who consistently overpay, underestimate, procrastinate, and stick to habited options. (Watzek, et al., 2019) (Ariely, 2008) (Henoker, 2022) Will the hallucinating, human-trained, training data biased and narrowly understanding artificial intelligence match well with and compensate for the apparent weaknesses of human cognition? (Dear, 2019)
The paper aims to create an initial understanding of the answers to the above questions in a military context. Firstly, the paper develops a simple model for military confrontation and opposing systems. Secondly, it introduces the changes already emerging through the wave of the 4th Industrial Revolution (Schwab, 2017) in the model and defines essential variables. Thirdly, it studies literature and analyses lessons of man-machine teaming identified elsewhere in industry, work, and society. Fourthly, the paper configurates the systemic model with the man-machine teaming lessons and games the confrontation with varied setups.
The Creation of a Model for Military Unit in Confrontation
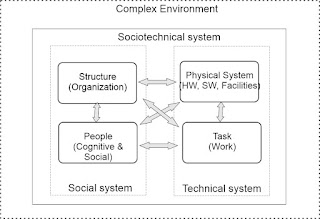
The section aims to create a simple model of military confrontation at the tactical level with both opponents described as socio-technical systems. The model shall support analysing variations of the man-machine system of systems components, interrelationships, and vulnerabilities in confronting two opposing parties.
Heinz Guderian (Guderian, 2001) designed the armoured combined arms Pantzer division supported by air-to-ground fires and revolutionised warfighting in early World War II. He used the later defined concept of a socio-technical system (Pasmore, 1995) to improve human-machine cooperation and initiative, trained standard processes through all troops, improve data flows through the use of field radios, and deployed tactical manoeuvre and firepower in a way that created strategic surprise among adversary forces prepared for more I WW era or even older ways of warfighting (Betts, 1980). He used two human cognitive level features that had been created within the German military: Staff officers' pattern recognition at the operational level (mission command) (Muth, 2013) and NCOs' initiative at the combat level (Widder, 2002). When focusing on the cognitive effects, artificial intelligence can impact military structure at the technical, tactical, and operational levels, including all traditional components and interactions of a socio-technical system (technical systems, organisation structure, cognitive and social features, and tasks) (Abbas & Michael, 2023)
Based on the socio-technical system structure, assuming the impact areas of artificial intelligence, and reflecting the lessons from Guderian's revolution, the composed military system model is illustrated in Figure 2, including:
- Human actors at the cognitive layer have social and moral cohesion as traditionally defined. (Pipping, 1947/2008)
- The process layer consists of both manual (man) and automated (machine) processes but also explains the performance of the function.
- The data layer is essential for the man's (cognitive) situational awareness and for the machine's ability to analyse through calculations.
- The algorithm defines the artificial intelligence actor in the system.
- Computational power is a technical feature that is becoming an essential enabler for artificial intelligence calculations.
The following section seeks lessons from other fields for man-artificial intelligence cooperation for later to vary those lessons in a military context.
Lessons from Man-AI Cooperation in Sense- and Decision-Making Challenges
Section searches literature to find features in man-machine cooperation and confrontation that may indicate promising compositions for winning strategies regarding sense-making and decision-making in complex situations.
Table 1 fuses the lessons collected from the literature research. These lessons support the simplified principles that in sense- and decision-making:
- A better integrated and mature system wins over a less integrated system.
- A self-learning algorithm wins over a combination-seeking algorithm in a strategy game.
- Computing power is less of a determining factor than data and algorithm quality.
- A higher cognitive force is superior to a lower-performing cognitive party.
Table 1: Fusion of lessons concerning human-machine interactions identified in games and expert work
|
Confrontation |
Wins |
Loses |
|
High cognitive
force against more volume of lower cognitive force |
High cognitive |
Low cognitive |
|
High algorithm
with fewer resources against low algorithm with more resources |
High algorithm |
Low algorithm |
|
Self-learning
algorithm against trained algorithm |
Self-learning |
Trained |
|
People with medium-level
algorithms and data against highly trained but less cooperating human experts |
People with AI |
High experts |
|
Highly automated
force with high data against high operational and high cognitive human force |
Machine |
Man |
|
Faster learning
algorithm against searching algorithm |
Faster learning
algorithm |
Optimising
algorithm |
|
More mature
process against less mature process |
More mature |
Less mature |
|
Combination of
specified algorithms against more narrowly optimised but isolated algorithms |
Combination |
Isolated |
Strategic Artificial Intelligence Gaming for Success in Military Confrontations
The section seeks to test different strategies in two-player strategic games (perfect and complete information in simultaneous zero-sum games (Rutherford, 2021)) and see if dominant or equilibrium strategies for winning can be found.
The existing organisational operation model defines the boundaries for an organisation's ability to develop and adapt new capabilities. The evolution of military enterprise -paper (Mattila & Parkinson, 2018) used an operation or process model dividing military enterprises into four categories: Diversified, Replicated, Coordinated or Unified.
Figure 3: Strategic posture and Operation model variations in military affairs
Melvin Conway (Conway, 1968) recognised a tendency of "Any organisation that designs a system will produce a design whose structure is a copy of the organisation's communication structure". In the same way, the military operational model in Figure 3 may reflect the generated capabilities following four stereotypical categories:
- The diversified operational model defines many current Services, which acquire, generate, and operate their forces independently from other Services. These military organisations are usually hierarchically arranged, and value is created vertically along the command lines. This operating model was typical in the WW I when infantry and artillery regiments fought their battles separately (Vego, 2009, pp. I-19). The siloed operational model may generate processes with a variety of maturity, lower-level data, various algorithms and computing, and varied levels of human competency and social cooperation.
- The replication operational model enhances operational efficiency by standardising the processes but not integrating them between Services. The goal is to execute standardised processes faster than the adversary or more cost-effective. NATO aims to standardise member state-generated force elements for multinational effects. Before WW II, the Western military was generating forces arranged in regiments by their branch (artillery, infantry, cavalry, engineers, signals) and learned only during the war to create multi-arms brigades for combined arms effect (Creveld, 1987, pp. 98-116). The siloed but standardised operation model may generate mature processes, lower-level data, and various algorithms and human cognition levels.
- The coordination operational model integrates different processes aiming to optimise operational efficiency. Joint operations (Vego, 2009) call for coordinated effects of force elements through multi-domain engagement . Coordination requires a pervasive command and control system. NATO aims to standardise member states' forces for better interoperability. A typical example is a combined arms brigade, where unified command and control make all arms and branches fight together (Creveld, 1991, pp. 98-116). Since the 1990s, a flatter, more connected organisation has been called a network-centric or enabled force (Vego, 2009, pp. XIII - 3). The integrated and coordinated operation model may generate mature processes and high-level data but various algorithms and human cognition.
- The unification operational model combines integrated processes and standardised force elements. The operating model aims to maximise operational effect and effectivity by combining different capabilities integrated into a Joint Force. Processes are owned by the Commander in Chief or his staff and developed centrally. The maturity of processes enables the deep specialisation of units since they are always used in combined arms, cross-domain and joint manner. McChrystal (McChrystal, et al., 2015, p. 115) created a force working as a team of teams – many similar special operations teams fighting against Al-Qaeda in Iraq as one extended enterprise. The unified operation model may generate mature processes, high-quality data, well-trained algorithms, and humans.
When the above operation model boundaries for development or adaptation are considered against the model's components illustrated in Figure 2, the matrix, presented in Table 2, projects the operation model boundaries to the socio-technical system model.
Table 2: Summarised man-machine capabilities from different military operational models and simplified to a performance number
|
Components/ Operational
models |
Human Cognition |
Process maturity |
Quality of data |
Algorithm |
Computer power |
Man-machine system performance |
|
Diversified |
Varied |
Wider
variety and maturity |
A
wider array of siloed data |
Sub-optimized
algorithms |
Varied |
1 |
|
Replicated |
More
homogenous but slow learning |
Standardised
but slower maturing |
Variety
but better-formalised data |
The
same algorithm for everyone |
The
same level of computer power for everyone |
2 |
|
Coordinated |
More
cooperative |
Integrated
so more cooperative |
Data
flows improve quality |
Improved
algorithms with shared data |
Connected
computers |
4 |
|
Unified |
Cooperative
and faster learning |
Connected
and faster maturing |
Quality
data to enable learning and training |
Enhanced
algorithms with quality data |
Optimised
power for each application |
5 |
Quantification in the last column indicates the effectivity of each approach measured as man-machine system performance. Evaluation is based on collected expert opinions. Gaming these different approaches against each other, one can see how the operation model that defines their developed man-machine capability will also determine their strategic outcome.
In game theory, a dominant strategy is a choice that is optimal for a player, regardless of what the other players do. (Rutherford, 2021) Using the operation model variant in conflict between two forces, BLUE and RED, and comparing their system performance extracted from Table 2, the strategy comparison is illustrated in Table 3. The rules in strategic, non-cooperative game in linear, symmetric confrontation are:
- Rule: Attacked needs at least two times better-performing force over a defender to win; otherwise, the result is either exhaustion or loss.
- Legend: -1 = loss; 0 = exhaustion; 1 = win.
Table 3: Payoff matrix between two military forces varying their operation model strategies and calculating conflict outcome based on the performance of their man-machine systems
|
|
RED |
||||
|
BLUE |
|
Diversified |
Replicated |
Coordinated |
Unified |
|
Diversified |
0, 0 |
-1, 0 |
-1, 1 |
-1, 1 |
|
|
Replicated |
0, -1 |
0, 0 |
-1, 1 |
-1, 1 |
|
|
Coordinated |
1, -1 |
1, -1 |
0, 0 |
-1, 0 |
|
|
Unified |
1, -1 |
1, -1 |
1, 0 |
0, 0 |
|
The operation model seems to have the main impact on the confrontation outcome. The dominant strategy (Rutherford, 2021, p. 34) for both players appears to be the unified strategy (emphasised in Table 3 in blue and red colours), which will be superior to all other operation models. The same strategic choice of a unified operation model seems to be the equilibrium way (Rutherford, 2021, p. 75). Neither of the parties will regret their choice. As the strategic game indicated that the operation model will be the significant indicator in the conflict, it needs to be reflected in two approaches: quantity and quality dominance on the battlefield.
In the pure attrition optimising conflict, the volume of combat power remains determining since massing a high number of man-machine teams against fewer adversaries has higher odds of winning in one-to-one and all-against-all situations (Lanchester I and II laws). (Johnson & MacKay, 2015) If we follow the logic of Stephen Biddle (Biddle, 2006), the quantity of force in battle is the outcome's primary definer. Furthermore, Lanchester's models support this approach. How does the operation model impact the quantity? A unified force, i.e., a joint force in a multi-domain battle, can optimise the engagement freely with any target. Other operation model forces have constraints in their firing and decision-making abilities. Hence, the conflicting parties are following different laws of Lanchester. The advantage of the Unified party becomes evident when modelled with the square law. In contrast, the other operation model party follows linear law.
On the other hand, if we follow Trevor Dupuy's (Dupuy, 1987) approach, the quality of force affects the battle outcome. From the analysis, we may conclude that a party whose quality of human-human and human-machine interaction is advanced is more likely to win if the conflicting parties' capabilities are otherwise even. It seems that improved data (pace, friction, quality), interfaces (human-machine and machine-machine), and social structures (e.g., trust, communication) decrease entropy and friction (Clausewitz, 1984) in a socio-technical system. Hence, the unified operation model will ensure future success more probably than other operation strategies.
Conclusion
The research question asked, "What happens when a 4th generation industrial artificial intelligence is introduced into a 3rd generation socio-technical military force?" or simplified, what combination of man and machine brings victory on the battlefield? The paper first creates a model for military force as a socio-technical system. Then, the article extracts lessons on artificial intelligence's effects on man-machine cooperation from other industries and businesses. Next, the military socio-technical system model varies with these 4th generation artificial intelligence lessons. Finally, different operation models are conflicted in strategic gaming. The results indicate two foundational principles for dominance: A unified operational model and improved man-machine cooperation.
The first result indicates that traditional massing of combat power will still explain dominance in foundationally attrition-focused battles. With artificial intelligence, enhanced cooperation of man-machine teams will provide more accurate effects, and massed firing will demoralise both human and artificial cognition. The combined, joint, and all-domain military capabilities seem superior against more segregated force structures.
Secondly, artificial intelligence will provide the best outcome measured in man-machine cooperation when applying the unified military operation model. The result explains the dominance of the unified military operation model in less attrition-focused battles. Artificial intelligence alone does not make the difference in broader socio-technical systems. Still, the combinatory effect of mature processes, quality of data, and robust trust between actors enable higher levels of military capability.
The paper provides a simple model for the military as a socio-technical system, which opens opportunities for a variety of other development or transformation studies besides the impact of artificial intelligence. Naturally, the model is simplified for this study and needs further modelling to be more explanatory. The first insights collected from the 4th Industrial Revolution look interesting and promising from the military viewpoint but require further testing before implementation. Nevertheless, the results of this paper are supported by existing trends and remind us that the focus was on how 3rd industrial military force would improve with artificial intelligence. The study does not refer to "Digi native" military affairs, which may introduce revolutionary ways of winning the battle.