1. Introduction
The first step in military socio-technical system evolution (Trist, 1981) was the creation of the Wehrmacht Panzer Division in cooperation with the Luftwaffe's air-to-ground support. (Guderian, 2001) The available industrial machinery, tank crew training based on professional warrant officers, and gradually challenging training matured a coherent team of men and machines who were aware of their strengths and weaknesses and trusted the support from other actors (e.g., commanders, artillery, engineers, signals, air support, logistics) of their combat power system.
After the blitzkrieg, the military has been trying to generate combined arms, Joint operations, and Combined operations capabilities with varyingly sourced force elements. (Vego, 2009) Figure 1 presents a hypothesis for the evolution of the military socio-technical system. Before digitisation, military organisations used weapons as tools, managed information manually on paper, and emphasised commander-centric decision-making. As weapons turned into platforms, the human operator merged with the machine. Information was digitised, and computers became interfaces to communications and knowledge. In the future, large platforms will turn into swarming, autonomous systems; data will be processed by learning computer algorithms; and commanders will be supported by their machine Companions in decision-making. Will this be the military socio-technical system in the future?
Figure 1: An evolutionary view of the military socio-technical systemThe military has a history of adopting technologies and methods from other domains of society. The values, education, and culture the society provides to its citizens also reflect on military socio-technical features:
- Russia aims to mass fire from automated weapon platforms (Mittal, 2022) without concern for collateral damage in operations (Lavrov, 2018).
- China installs autopilots on old fighter aircraft to create swarms of targets and educates its commanders in computer-simulated battlefields .
- The USA has a long history of remote-controlled Unmanned Aerial Systems (UAS). It currently operates unmanned systems in all five domains.
Technology is transforming governments (eGovernment) , industrial manufacturing and logistics (4th Industrial Revolution) (Schwab, 2017), retail (Amazon ) (Hagberg, et al., 2016), transportation (Uber and Green Deal) , social life (cogni-tech) (ESPAS, 2018), working (gig economy) and creative production (ChatGPT) . There are opinions (Oliviero, 2021) (Biddle, 2006) that technology has been the servant of military ideas: ideas create concepts, concepts create intellectual structures, and intellectual structures drive technological change in military organisation. So, despite the revolutions in surrounding societies, the military has to invent emerging technology rather than adapt to changes in their environment. The complex, adaptive system theory opens other views to military evolution. (Jackson, 2019) A combination of determined and complex ideas produces three paths for socio-technical system development (Mattila, 2020)
- Preadaptation is driven by the need to develop a new System of Systems. It includes research, experimenting, or learning new knowledge with other means. Several optional solutions may be produced and explored to find the best fit. Gained knowledge and prototypes are used to design a new system to fulfil the requirements of the new function.
- Adaptation happens when the System of Systems is co-opted gradually for different uses without a broader comprehension of the evolution.
- Exaptation occurs when a component from another system is co-opted as part of a new System of Systems, making it more efficient or fitting for the purpose.
The article aims to create a tactical engagement model to answer the question -What may be the military future with artificial cognition as part of their socio-technical system? The building of the model starts by reviewing man-machine interface evolution, then extends to the man-machine cooperation as part of a more extensive system, uses network theory to define other dimensions of the military socio-technical system, introduces an army confrontation model at a tactical level, and, finally, composes a simplified model for the tactical engagement as an open, complex, adaptive socio-technical system.
2. Evolution of Man-machine Interface
The model creation starts from the interface of how a man and his machine communicate. The paper combines three evolutionary interface paths: industrial terminals, cockpits in aircraft and computers in an office. The evolution of the industrial operator terminal interface (Papcun et al., 2018) indicates the tendency for symbolic and manual communication when man-machine cooperation is not continuous. Still, the operator roams between different terminals on the factory floor. (Buxbaum-Conradi, et al., 2016)
A different situation is in the cockpit of an aircraft. The pilot faces the aircraft interface throughout the flight and monitors it even when the craft is on autopilot. In the cockpit, the tendency has been to present information fitting to the constraints of human sensors in stressful situations while keeping the pilot's visual view as clear as possible to surrounding airspace. Naturally, radars and infrared sensors have widened the spectrum of optical sight and introduced synthetic vision.
Again, a different story is with the interface of office computing. The interface of screen, keyboard, and mouse since the late 1980s has seen minimal changes for an ordinary knowledge worker. For engineers and graphic designers, the workstation interface appears more applied. Naturally, the ongoing expansion of mobile devices has replaced keyboard and mouse with audio, video, and touch as the content has also evolved from text to multimedia. On the other hand, digital content creation accelerated the evolution of the personal computer as a portal to a wide variety of business, governmental, social, financial, and other everyday related content and transactions. Figure 2 provides a combined view of interface evolution in different environments.
Figure 2: Samples of man-machine interface evolution from three environments: factory, aerospace, and knowledge work (CC-BY-ND Juha Kai Mattila)Conclusions from the interface evolution model:
- The tendency seems to lead to a more human-friendly interface between humans and machines. Interaction through touch, audio, synthetic video, and hand movements in virtual or augmented reality may be the next step the military may adopt from elsewhere in society.
- More cognitive, non-intrusive or intrusive links between human thinking and artificial intelligence may emerge.
- A stressful environment narrows the human ability to receive and comprehend information. Hence, artificial cognition-enhanced situational awareness, process automation, and autonomous action may be appreciated on the battlefield.
3. A Model for a Man-machine Cooperation as Part of a Larger System
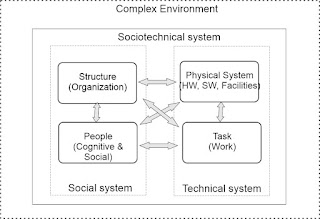
The socio-technical system theory (Trist, 1981) provides a broader framework to study man-machine cooperation. The socio-technical system comprises two subsystems (social and technical) in interaction with the environment, as illustrated in Figure 3. The social system includes individuals or teams that constitute an organisation. The organisational members deliver the relationships, values, structure, work-related elements, and associations. (Pasmore, 1995) The technical system includes the physical, material, and information flows required in the value creation process and tasks, controls, and maintenance functions. In the organisational setting, the technical system also includes the tools, techniques, skills, and devices that people require to fulfil enterprise purposes and tasks. (Trist, 1981) The environment is the context, surroundings, and conditions in which the open socio-technical system resides, operates, and interacts. (Abbas & Michael, 2023)
The model presents a human-oriented social system following different principles than the machine-oriented technical system but promoting a joint optimisation or equilibrium, which is a degree of fit or balance between the subsystems. Cybernetics (Wiener, 1954) introduce organisational entropy and information-based evolution of complex systems. These two theories explain transformation challenges when new technology and existing human competency do not fit each other, organisational change does not align with existing informal social connections, or the current system is profoundly stabilised, resisting all transformation initiatives.
Figure 3: A model of a socio-technical system
Conclusions from the socio-technical model:
- The process is a critical subsystem which interrelates with the organisation, people and technical systems.
- The social system will be exposed to cognitive artificial entities and social relations created between these entities and men. The fast surge of ChatGPT and video game popularity indicates that men may be keen to communicate with reactive chatbots. Will this interest overcome the suspicions in alien encounters, and how much training will it take for men to trust artificial entities for their survivability on the battlefield?
- The joint optimisation between the subsystems seems essential for the digital transformations of the military enterprise. Technology-driven change fails if soldiers' competencies and social behaviour are not transferred simultaneously. Conversely, a lack of technology drives people to use other available means of communication, establish unofficial networks, and accomplish tasks.
- The organisation has been structuring the social networks between people. With artificial intelligence, the organisational structure may experience significant changes when new cognition finds ways of working beyond human imagination.
4. Network Models for Large Systems
The theory of Actor-Network, ANT (Latour, 2005) introduces a broader model to study man-machine systems. The ANT does not differentiate humans from machines or processes in a network. The ANT defines three network layers: real world, symbolic and imaginary, as illustrated in Figure 4. The real-world network presents human–machine–machine–process links between actors whose activity is required to deliver the intended outcome. The symbol network reflects the real-world network topology. Still, it presents the different symbols in which actors understand the situation and task. For example, as the organisation is a social network, this level reflects both the official and unofficial networks using different symbols between people and their attitude to the task ahead. (Kadushin, 2012) The third layer illustrates the imaginary view of the event, where humans and artificial intelligence-enabled machines may perceive the situation differently in the future.
Figure 4: A simple representation of close air support delivery on ANT layers (CC-BY-ND Juha Kai Mattila)Conclusions from the model:
- The ANT layers illustrate the interdependencies and interoperability challenges between actors to achieve a task. No actor can accomplish the job alone but depends on others' coordinated contribution. Every link between actors has three different information transfer levels.
- The symbol network illustrates that understanding differs from one system to another. Humans understand events differently than machines, so symbols and meanings alter while passing the man-machine interface. Moreover, devices use different logic and may understand the same event contrarily from humans. With artificial intelligence, socio-technical system integration becomes more critical when militarily trained humans are not translating information from one machine to another.
- While daydreaming is human and their misperceptions create errors, artificial intelligence also hallucinates and may promote failed resolutions. How these two species with different imaginary features can cooperate in stressful situations?
5. Modelling Military Engagement at the Tactical Level
Traditionally, the engagement at the tactical level has been a contest between two commanders (Oliviero, 2021). Both commanders use combat power, defined as the ability to manoeuvre, mass effects, fire, and maintain tempo orchestrated through all five domains (space, air, cyber/electromagnetic, land and maritime) on the battlefield. (Friedman, 2017) Besides the physical destruction, both sides use their combat power to deceive, surprise, confuse, or shock the other side's cognitive level and aim to disintegrate social and moral cohesion. The operational level may use information and psychological operations to weaken adversaries at social and mental levels in support of tactical combat. (Vego, 2009) Figure 5 illustrates the engagement model.
Figure 5: Modelling tactical actors, tenets, and their relationships in confrontation (CC-BY-ND Juha Kai Mattila)Conclusions from the model:
- Machine intelligence will increase cognitive vulnerabilities in deception, confusion, and shock when they face an event beyond their training data. Is there a human on the loop to detect this and configure a machine to adapt to unseen situations?
- The Man-machine interface has often been the breaking point of the cohesion of military units. A crew abandon their vehicle when they are afraid of their survivability. How do humans trust algorithms in tight situations?
- Engagement in five domains and projecting effect to adversary systems through tactical tenets become complex for humans to control. A commander requires an artificial enabler (Companion) to understand the situation, choose cost-effective targets, and optimise effectors used on the battlefield.
6. A Composed Model for the Research
From the above frameworks, the paper chooses to compose a simplified model in Figure 6 to study the opportunities and challenges of introducing artificial intelligence in military systems at a tactical level. The composition of the Blue and Red units is assumed to be the same. Still, the differences in adopting artificial intelligence may produce different outcomes on the battlefield. The model reduces all information and communications technology to computational power. Artificial intelligence is in algorithms and includes both preprogramming and self-learning. Data indicates the symbolic layer in the technical system and cognition in a social system. The process is an essential socio-technical system including interfaces, tools, skills, procedures, and doctrines that make the military system cooperate. Social structures include both man-to-man, machine-to-machine and man-to-machine relationships. Culture is in the background, impacting everything from algorithms to social structures. A simplified tactical engagement between the systems will provide a testing ground for the outcome of the confrontation.
Figure 6: The core actors, interfaces, and dependencies of a jointly optimised socio-technical and networked system in a tactical confrontation (CC-BY-ND Juha Kai Mattila)Further research will use the above model to study what possible effects improved algorithms may introduce in military enterprises, especially in tactical engagement.