"Thoughts without content are empty, intuitions [perceptions] without concepts are blind"
Immanuel Kant
A Story
A fictional discussion in RED and BLUE Ministries of Defence:
- RED Minister of Defence: "Let’s build up the strength of our standing force from 1 000 000 soldiers to 1 200 000, improve the operational transportation speed of our railways from a brigade/100km/2hrs. to a brigade/100 km/1hr., and establish new factories that can manufacture ten main battle tanks per day.”
- BLUE Operational Commander after the Intel brief: “RED is aiming to improve their land component operational capabilities to achieve a mass advantage in any part of the area of operation. I need four mechanised brigades to counter the emerging capability within the next three years.”
- BLUE Land Force Commander: “We do not have tanks, ammunition, mechanised troops, trained tank crews, antitank weapons, air defence, supporting fires, signals, engineers, logistics or facilities to generate four mechanised brigades. Armament acquisition takes at least four years, building training facilities takes five years and generating troops takes minimum two years. Each brigade will need at least 500 million investment and produces 50 million annual operational costs.”
- BLUE Armed Forces Commander: “We do not have the budget nor time to meet the operational demand. Are there other options to address the emerging threat but building symmetric forces?”
- BLUE Minister of Defence: “Now is not a good time to propose an increased defence budget because elections are within 1.5 years, and popular opinion demands health care for increasing elderly population. What is the probability that RED will use this increased military power against us?”
Approaches to Military Capability Development
Developing military capabilities is always a balanced decision between different contents and contexts projected against variety of probable threat scenarios. European Armed Forces are restoring their capabilities in competition with Russia's accelerated military industry and force generation. Some countries have selected to build symmetric armament, others apply modern technology to squeeze more lethal power from their existing capabilities, and some do what they can in current circumstances.
In every case, the decision-making in capability building is not an easy task since every decision or non-decision impacts the Armed Forces over an extended time and may lead to peril when threats against national security unfold differently than assumed in environment illustrated in Figure 1. Furthermore, maintaining a portfolio of Military Capabilities is affected, for example:
- Biased and noisy decision-making in an organisation (Kahneman; Johnson; Heat)
- Path Dependence (Liebowitz & Margolis)
- Political guidance (Gray)
- Society´s resources and culture (Bousquet)
The following process brings some systematic analysis and assessment for the military capability planning to provide longevity, balanced sense-making from different points of interest and continuous evaluation of the situation.
Figure 1: Blue vs. Red military might
Building a Concept for Military Capability Development Decision Support
The analysis and assessment process for capability development uses the SDLC V-model originally created for developing and testing software artefacts, illustrated in Figure 2. The V-model down-slope analysis follows Kahneman's decision-making strategies utilizing, for example, the following methods:
- Clustering follows loosely the US DoD DOTMLPFII-programme evaluation model but with added Budget checkpoint
- The concept of Operation uses a standard military CONOPS creation methodology.
The V-model up slope assessment uses operational research methodology, e.g.:
- Tactical Assessment utilises Lanchester models,
- Operational Assessment deploys QJM models,
- Strategic Assessment uses systems thinking models of consumption of strategic assets, and
- Political Assessment experiments Threat/Prospering Balancing models.
Detailing the Capability Development Analysis and Assessment Process
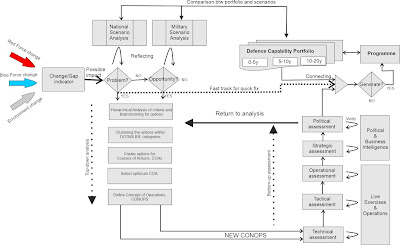
The process, as illustrated in Figure 3, main functions work as follows:
- Military capability analysis receives its input from the changes in potential adversaries (RED) via intelligence information, own forces (BLUE) via business intelligence, or environment (Political, Economics, Sociological, Technological, Legal, Environment [PESTLE])
- The change indicator recognises the change (military intelligence) and possibly pre-estimates its impact.
- A detected and identified possible impact is forwarded to problem and/or opportunity analysis. This analysis uses existing national defence and military scenarios to detect whether the change is an opportunity or a problem. During the analysis, the key performance indicators for the solution are defined.
Whether a problem or an opportunity is detected, the top-down analysis is commenced. Suppose the problem has surprised BLUE or evolves faster than BLUE expects. In that case, a fast track forwards a quick fix directly to connecting, where urgent need is fitted into the ongoing force generation process and transformation programme is launched.
- Problem seeks solutions first parallel through DOTMILBIE (B=budget, E=Equipment) phases, and if it is not found, then proceed towards E until there is a solution that meets the given KPIs.
- Opportunity seeks possibilities to gain advantages over the RED through a similar sequence of analysis.
The top-down analysis provides a concept of operations (CONOPS) for bottom-up assessment to define the detailed design with a sequence of different level war games. The assessment includes the sequence of:
- The technical assessment compares the solution/possibility concept against the current and emerging technical capabilities of an adversary
- The tactical assessment compares unit-level combat outcomes and varies with strength, lethality, and protection
- The operational assessment compares force-level battle outcomes and varies with the area of operation, mode of operation, weather, and quality of troops.
If similar conditions exist, the three wargaming results are verified in live exercises or operations. The wargaming models learn from lessons identified in the live world.
- Strategic assessment compares defence-level assets over time and optimises their sustenance over various operations, environments, resources and crises. The assessment is verified using business intelligence collected from BLUE Force over time.
- The political assessment reflects the current and future geopolitical, decision making and other PESTLE-related features at the national political level. The assessment is verified using political intelligence collected from international relationships and political decision-making.
Once the top-down concept is assessed through levels of the bottom-up approach, the resulting solution should be considered, optimised and balanced from DOTMLPFII viewpoints and tested successfully at five levels of current and future confrontation. If not, the CONOPS is returned to the analysis process for reconsideration.
The optimised solution continues to the connecting function, where the solution is compared with the existing capability portfolio (composed of three windows: Current, in Generation, and in Planning). Once the suitable timeslot and financing are found, the optimised solution can be introduced to decision-making: Generate new capability or manage the risk other way. If the decision is towards development, a generation programme becomes a part of a 5-10-20-year plan.
During the defence capability portfolio management, the ongoing programmes are continuously compared to national defence and military scenarios and adjusted per emerging needs.
.
Figure 2: A simplified process for military capability development decision support
The above systematic capability analysis and assessment process provides:
- Continuous and faster analysis and assessment cycle (years to months) than one-time efforts in slower frequency,
- Faster learning process with improved connectivity to data sources than with only manual research and assessment,
- Systematic and less biased/noisy process that survives officer rotation than human-centric and dependent process, and
- Accumulating a knowledge base that enables further automation enhanced with business intelligence, modelling and simulation, wargaming and digital twins.